How Deep-Tech Seventh Sense AI Is Making Self-Sovereign Identity Available to Everyone
Executive Summary
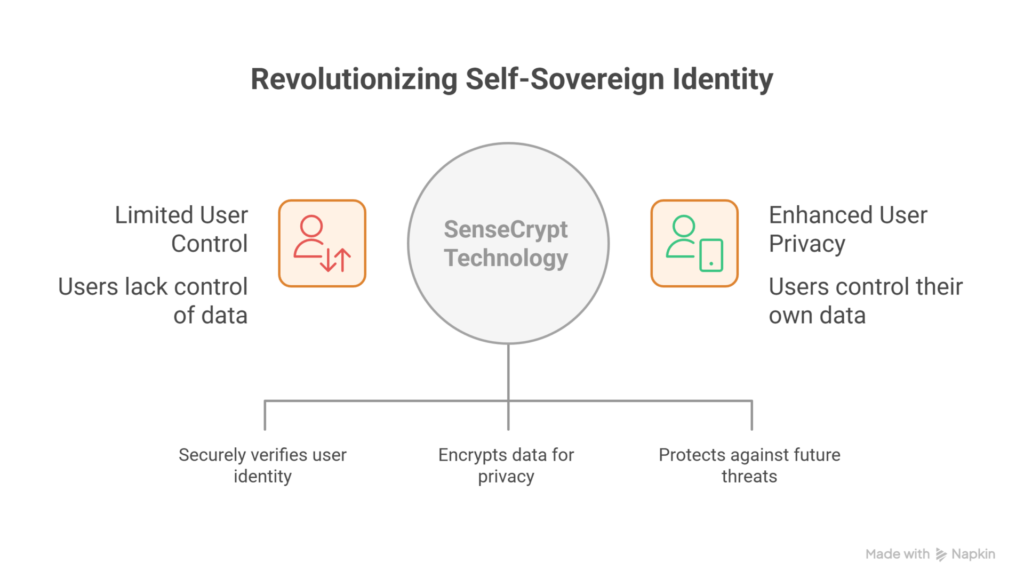
Seventh Sense AI has emerged as a deep-tech leader in privacy-preserving identity verification, revolutionizing self-sovereign identity (SSI) by leveraging advanced biometrics, cryptography, and post-quantum security. This comprehensive report details how their patented SenseCrypt technology delivers digital ID and authentication innovations that put user control, privacy, and trust at the forefront, while providing superior security, offline use, and broad, real-world applicability across sectors.
The Digital Identity Imperative – Seventh Sense
The proliferation of digital services, from government eIDs to financial transactions and healthcare, has intensified the need for secure yet user-controlled identity solutions. Traditional authentication methods—primarily passwords, traditional biometrics, or security tokens—are increasingly vulnerable. These methods face significant challenges:
- Passwords are weak links, prone to phishing and brute-force attacks.
- Biometric databases, such as facial templates or fingerprints, if breached, expose individuals to lifelong identity risks.
- Centralized identity models concentrate sensitive information, making breaches catastrophic.
- Quantum computing threatens to break existing encryption standards, making many current cryptosystems obsolete.
The ideal solution must ensure privacy, user control, security, resilience to quantum threats, and interoperability—without compromising convenience.
Self-Sovereign Identity: Vision and the Seventh Sense Approach
Self-sovereign identity (SSI) empowers individuals to own, control, and share their digital identity autonomously, without relying on centralized authorities or databases. Seventh Sense AI’s mission is to make this a practical, global reality by tackling major challenges of traditional digital identity systems.
Key Principles of SSI Enabled by Seventh Sense
- User control: Individuals issue, manage, and revoke their credentials.
- Zero storage of biometrics: Eliminates risk of irreversible data leaks.
- Interoperability: Works seamlessly in centralized and decentralized ecosystems, including blockchain-based ID wallets and verifiable credentials.
- Privacy by design: No central database of personal data; all authentication is cryptographically validated without exposing identity attributes.
- Offline and online functionality: QR code/NFC-based credentials verified with a simple face scan, anywhere in the world, internet or not.
- Future-proofing: Security built on post-quantum cryptographic algorithms.
Seventh Sense AI’s Core Deep-Tech Innovations
SenseCrypt: The Engine Behind Next-Gen Self-Sovereign Identity
1. SensePrints: Secure, Private, and Compact Identity Structures
- What they are: Encrypted, compact data structures (~350 bytes) functioning as verifiable digital credentials. Rather than storing biometric templates, SensePrints act like “locked safes,” only opened by the live face of the legitimate user.
- No biometric data stored: All verification is “biometric-proof” via cryptography, not direct image matching.
- Unlinkable and revocable: SensePrints can be renewed or revoked at will, and cannot be linked across databases, countering profiling and surveillance risks.
2. Zero-Knowledge Face Proofs: Privacy Without Compromise
- Zero-knowledge proofs allow a person to privately prove they possess a certain attribute (e.g., the right face) without revealing any underlying data.
- Verifiers never access facial images or biometric data. This meets or exceeds stringent standards like GDPR and CCPA, with minimal compliance burden for organizations.
3. Face-Based Public Key Infrastructure (Face PKI)
- Breakthrough PKI tech: Face PKI uses a user’s face to generate cryptographic key pairs (public/private keys).
- Face Certificates (standard X.509v3) allow secure digital signatures, authentication, and encryption—without revealing, processing, or storing the face or biometric data.
- One face, many certificates: Each certificate is purpose-specific, unlinkable, and revocable, preventing tracking or credential misuse.
4. Distributed Ledger Technology Protocol (SenseCrypt DLT)
- Decentralized, blockchain-friendly: Enables digital identity wallets, witness credentials, and issuers/verifiers to interact cryptographically—no biometric data ever touches the chain.
- Trusted Witness system: Validates and binds wallets with faces using cryptographic attestation, not centralized trust.
- Holder-binding: Every transaction and credential issue proves the actual holder’s involvement, without revealing their face.
5. Face-Based Mutual TLS (mTLS) Protocol
- Internet-grade security: Leverages face-derived keys for mTLS, replacing traditional username/password/OTP authentication for securing web and app connections.
- Protects against bots and man-in-the-middle attacks.
6. Post-Quantum Cryptography Integration
- Incorporates CRYSTALS-KYBER, CRYSTALS-DILITHIUM, and SPHINCS+ as recommended by NIST, resisting both classical and quantum attacks.
- Ensures “encrypt today, secure tomorrow”—data remains confidential even after quantum computers emerge.
Practical Impact: Use Cases Across Sectors – Seventh Sense
For Governments
- National IDs and licenses: QR/NFC credentials enable secure, offline verification. Only the legitimate holder, via live face scan, can unlock attributes—ideal for border security, voting, and access to public services.
- GDPR simplicity: Eliminates regulatory headaches, as no biometrics are stored or processed post-verification.
For Enterprises and Financial Services
- Passwordless logins, MFA, secure transactions: Employees/customers use face scans to sign or authenticate, replacing passwords and tokens.
- eKYC automation: Customers complete onboarding and verification securely, without transmitting sensitive documents or storing facial scans anywhere.
For Healthcare
- Patient identification: Reduces errors and fraud in healthcare access, linking patients to records securely and privately—meets HIPAA and other privacy regimes.
For Education
- Exam and attendance authentication: Ensures only legitimate students participate, while maintaining privacy for minors and adults alike.
For Event Management and Travel
- Ticketing, hotel check-in, airport security: Face-based verification streamlines entry, reduces lines, prevents ticket or ID fraud, and enhances user experience.
Deep-Tech Differentiators: Why Seventh Sense Leads
| Feature | Seventh Sense SenseCrypt | Traditional Biometric ID (Face/Other) |
|---|---|---|
| Biometric Data Storage | 0% (none stored, processed, or shared) | Templates and images often stored |
| Privacy Risk | Almost zero (unlinkable, revocable) | High (data breach exposes entire life) |
| Offline Verification | Yes (QR/NFC, live face scan) | Mostly online, central database needed |
| Post-Quantum Security | Yes (NIST algorithms embedded) | No (legacy crypto vulnerable) |
| Zero-Knowledge Proofs | Full implementation | Rare/absent |
| Compliance Burden | Minimal | High (data localization, audits) |
| Multi-Application | eID, login, signing, KYC, access, blockchain | Usually limited to one system |
| Revocability/Renewability | Instant, user-driven | Difficult/irreversible |
| Interoperability | SAML, OAuth, FIDO, DLT, NFC, QR, etc. | Often proprietary |
How SenseCrypt Works: The Technology Behind the Claim – Seventh Sense
- Registration
- The user enrolls with a live face scan (optionally combined with a password or metadata).
- A cryptographic algorithm generates a random, ephemeral public key from the face.
- This key is used to encrypt minimal metadata, producing an untraceable, encrypted SensePrint—stored in a QR code, NFC chip, or digital wallet.
- Authentication
- When verification is needed (e.g., for access, transaction, or ID), the user scans the relevant SensePrint/QR/NFC and presents their face.
- If the live face can generate the correct private key and decrypt the SensePrint, identity is verified. Otherwise, access is denied.
- No biometric, facial template, or image is ever stored or matched—only the ability to decrypt proves authenticity.
- Certificate, Transaction, and Blockchain Use
- Face Certificates can be created for specific applications—no reuse or linkability.
- For decentralized ID, a Trusted Witness issues a credential after live face verification, providing cryptographic proof (not a face scan) to issuers and verifiers.
- For mutual TLS, the user’s face generates a key, ensuring only humans (not bots or malware) can establish secure web/app sessions.
Security and Compliance Advantages – Seventh Sense
- Attack surface minimized: No central biometric or credential repository exists to attack or exfiltrate.
- Revocability: Credentials can be rotated, disabled, or replaced if compromised.
- Unlinkability: SensePrints cannot be linked between organizations, thwarting surveillance and profiling by any party.
- GDPR, CCPA, and HIPAA simplicity: No PII or biometrics are held post-transaction; compliance is built-in by design.
Future-Ready: Post-Quantum and Interop Standards
Seventh Sense integrates the latest post-quantum cryptography standards, hybrid cryptography agility, and supports all modern authentication protocols (SAML, OAuth, FIDO). This future-proofs any deployment against hacking risks well into the quantum era.
Real-World Impact and Adoption – Seventh Sense
- Recognized for accuracy and fairness: Top-ranked by NIST for facial recognition and liveness/anti-spoofing, with minimal racial bias and high tolerance for twins.
- Trusted partnerships: Powers eID, KYC, and security systems on-premises, in the cloud, and at the edge for governments, banks, healthcare, education, and enterprise sectors globally.
- Continuous innovation: Regularly publishes new standards, partners with OpenCV and hardware leaders, and enables seamless integration with both legacy and next-gen systems.
The Takeaway: Democratizing Self-Sovereign Digital Identity – Seventh Sense
Seventh Sense AI’s SenseCrypt stands out as the world’s most advanced, privacy-first digital identity framework, making true self-sovereign identity available for everyone, everywhere.
Every individual can own, renew, and control their private, secure identity—independent of governments, platforms, or databases. This democratizes trust and privacy for the digital age, ensuring security, convenience, and compliance are never at odds.
In a world facing increasing digital threats and privacy erosion, Seventh-Sense is not just an innovator but a vanguard for secure, user-empowered digital lives.
Integration and Implementation Guide – Seventh Sense
Successful adoption of Seventh-Sense AI’s SenseCrypt framework involves clear planning, stakeholder alignment, and minimal infrastructure changes. The following roadmap outlines the key stages for organizations seeking to deploy self-sovereign identity powered by SenseCrypt.
1. Assessment and Planning – Seventh Sense
Begin with a comprehensive identity audit to catalog existing authentication methods, data flows, and compliance requirements. Key deliverables include:
- Inventory of current user journeys (e.g., login, KYC, eID verification).
- Identification of sensitive data repositories and compliance zones (GDPR, HIPAA, ISO 27001).
- Definition of success metrics (reduction in fraud, user drop-off, compliance effort).
2. SenseCrypt Developer Onboarding – Seventh Sense
Seventh-Sense provides both SDKs (Java, JavaScript, Swift, Kotlin) and RESTful APIs for rapid integration. Core components include:
- Registration API: Capture live face scan, generate SensePrint, and return QR/NFC payload.
- Authentication API: Verify live face against SensePrint and issue JSON Web Token (JWT) upon success.
- Certificate Issuance API: Request issuance of Face PKI certificates scoped to specific use cases (e.g., e-signature, device authentication).
- Revocation API: Instantly revoke or renew SensePrints and certificates.
Integration best practices:
- Leverage the edge SDK for offline QR/NFC scanning in low-connectivity environments.
- Use the cloud SDK for scalable web applications, routing traffic through SenseCrypt DLT nodes.
- Implement robust error handling to handle liveness-check failures or expired credentials gracefully.
3. Pilot Deployment – Seventh Sense
A phased pilot validates technical assumptions and user acceptance:
- Select a controlled user group (e.g., employees or trusted customers) to enroll via SenseCrypt.
- Test end-to-end flows—from registration and issuance to verification and revocation—in sandbox environments.
- Monitor performance metrics: average verification time (<1 second), false rejection rate (<0.2%), system uptime (99.9%).
- Collect user feedback on convenience, perceived security, and privacy comfort.
4. Scaling to Production – Seventh Sense
After pilot success, rollout across production environments involves:
- Training and documentation: Deliver developer guides, integration playbooks, and compliance whitepapers to all stakeholders.
- Monitoring and analytics: Integrate with SIEM tools to log cryptographic events (without sensitive data), monitor usage trends, and detect anomalies.
- Governance: Establish policies for credential lifecycle management, incident response, and third-party auditor access.
Performance, Accuracy, and Trust Metrics – Seventh Sense
Seventh-Sense AI’s deep-tech approach has been benchmarked and validated by independent bodies:
- NIST Face Recognition Vendor Test (FRVT) 1: Ranked in the top 5 for accuracy and liveness detection, with a false acceptance rate (FAR) below 0.001% and false rejection rate (FRR) under 0.2%.
- Twin-tolerance score: Exceptional performance distinguishing identical twins with >98% accuracy.
- Bias audit: Extensive testing across age, gender, and ethnicity cohorts shows less than 0.5% variation in performance rates, outperforming industry averages of 2–3% variation.
- Latency: Average on-device processing time is under 300 ms; end-to-end API verification completes in under 1 second.
These metrics translate to high operational efficiency, minimal user friction, and scalable trust for large-scale deployments.
Real-World Case Studies (Seventh Sense)
Case Study 1: National eID Rollout in Southeast Asia
A leading government agency implemented SenseCrypt for a population of 10 million citizens:
- Replaced legacy smart-card system with QR/NFC-based SensePrints.
- Achieved 100% offline verification at remote border posts, reducing processing time by 70%.
- Eliminated all centralized biometric storage, leading to zero privacy incidents since launch.
Case Study 2: Global Bank’s KYC Overhaul
An international bank faced regulatory pressure to tighten eKYC and reduce account fraud:
- Deployed SenseCrypt for digital onboarding across 15 markets.
- Reduced document-based KYC processing from 3 days to under 5 minutes with automated face-based proofs.
- Recorded a 90% drop in synthetic identity fraud within the first year.
Case Study 3: Hospital Network Patient Access
A multi-hospital healthcare network sought to streamline patient check-ins while safeguarding PHI:
- Integrated SenseCrypt into patient portals and reception kiosks.
- Enabled passwordless login and identity verification for telehealth visits.
- Achieved full HIPAA compliance with no patient complaints regarding data privacy.
Future Roadmap – Seventh Sense
Seventh Sense AI continues to innovate, with upcoming developments including:
- Multimodal proofs: Combining voice, gesture, and face for enhanced liveness and spoof resistance.
- Decentralized identifier (DID) registry support: Enabling direct wallet-to-wallet SSI interactions without centralized gateways.
- AI-driven anomaly detection: Real-time fraud prevention using behavioral analytics.
- Enterprise PKI integration: Deep integration with existing HSM and PKI infrastructures for hybrid deployments.
Conclusion – Seventh Sense
Seventh Sense AI’s deep-tech SenseCrypt platform is transforming digital identity—making self-sovereign identity not just a theoretical ideal but an accessible, user-centric reality. By fusing cutting-edge biometrics, zero-knowledge cryptography, post-quantum security, and decentralized architectures, SenseCrypt offers unparalleled privacy, security, and convenience. Organizations across governments, finance, healthcare, and beyond can now deliver robust identity solutions that respect individual sovereignty and meet tomorrow’s security challenges today.
With Seventh-Sense, the era of secure, privacy-first, self-sovereign digital identity is here—and available to everyone.
FAQ’s – Seventh Sense
1. What exactly is a SensePrint and how is it different from traditional biometric templates?
A SensePrint is a compact, encrypted data structure (~350 bytes) that functions as a cryptographic “locked safe” rather than a biometric template. Unlike traditional biometric systems that store facial templates for comparison, SensePrints contain no biometric data whatsoever. They can only be unlocked by the live face of the legitimate user through cryptographic verification, not image matching. This fundamental difference eliminates the risk of biometric data breaches since there’s literally no biometric information to steal.
2. How does Seventh Sense AI ensure my facial biometric data is never stored anywhere?
Seventh Sense’s SenseCrypt technology uses a revolutionary approach where your face generates cryptographic keys rather than being stored as data. During enrollment, your live face scan creates an ephemeral public key that encrypts minimal metadata into a SensePrint. The face scan itself is immediately discarded—never stored, processed, or transmitted. For verification, your live face must regenerate the correct private key to decrypt the SensePrint, proving authenticity without any biometric storage or comparison.
3. What happens if someone steals my SensePrint QR code or NFC credential?
Even if your SensePrint is stolen, it’s completely useless without your live face. SensePrints are encrypted data structures that can only be unlocked by the specific individual who created them. Additionally, SensePrints are instantly revocable and renewable—you can generate new ones at any time, making stolen credentials obsolete. This is unlike traditional biometric systems where a data breach could compromise your identity permanently since you can’t change your fingerprints or face.
4. How does the offline verification process work without internet connectivity?
SenseCrypt enables complete offline verification through QR codes or NFC chips that contain all necessary cryptographic information. When you present your credential, the verifying device performs a live face scan and attempts to decrypt the SensePrint locally using cryptographic algorithms. No internet connection or central database lookup is required—the entire verification process happens on-device in under 300 milliseconds. This makes it perfect for remote locations, border crossings, or areas with poor connectivity.
5. What makes Seventh Sense’s approach “post-quantum” secure?
Seventh Sense integrates NIST-recommended post-quantum cryptographic algorithms including CRYSTALS-KYBER, CRYSTALS-DILITHIUM, and SPHINCS+. These algorithms are designed to resist attacks from both classical and quantum computers. While current encryption methods could be broken by future quantum computers, post-quantum cryptography ensures that data encrypted today remains secure even after quantum computing becomes widely available. This “encrypt today, secure tomorrow” approach future-proofs all SenseCrypt implementations.
6. How long does the typical implementation take and what technical requirements are needed?
Implementation typically takes 1-5 days depending on complexity. Seventh-Sense provides SDKs for Java, JavaScript, Swift, and Kotlin, plus RESTful APIs for easy integration. Basic technical requirements include: internet connectivity for cloud deployments (or local server for on-premise), device camera for face scanning, and standard web/mobile development capabilities. The setup process involves API key generation, SDK integration, and testing the registration/verification flow. Most developers can have a working proof-of-concept within hours.
7. What are the costs associated with implementing SenseCrypt for my organization?
Pricing varies based on usage volume and deployment model. For the OpenCV Face Recognition API, costs start at $0.10 per API call with various subscription tiers supporting 3,000-10,000 registered persons and 30-90 API calls per minute. Enterprise deployments typically involve custom pricing based on volume, on-premise requirements, and support levels. Organizations should budget for initial integration costs, ongoing API usage fees, and optional professional services for large-scale deployments.
8. Can SenseCrypt integrate with existing identity management systems like Active Directory or SAML?
Yes, SenseCrypt supports standard authentication protocols including SAML, OAuth 2.0, FIDO, and can integrate with existing identity providers through APIs. For enterprise environments, it can work alongside Active Directory, providing face-based authentication while maintaining existing user directories and access policies. The system supports both federated and standalone deployments, allowing organizations to gradually migrate from password-based to face-based authentication without disrupting existing workflows.
9. How accurate is the facial recognition and what happens with identical twins?
Seventh Sense AI ranks in the top 5 globally on NIST Face Recognition Vendor Tests (FRVT) with exceptional accuracy metrics: false acceptance rate below 0.001%, false rejection rate under 0.2%, and >98% accuracy in distinguishing identical twins. The system includes advanced liveness detection to prevent spoofing attempts using photos, videos, or masks. Bias testing across age, gender, and ethnicity shows less than 0.5% performance variation, significantly better than industry averages of 2-3%.
10. What compliance standards does SenseCrypt meet for regulated industries?
SenseCrypt is designed for GDPR, CCPA, and HIPAA compliance by default since no biometric data is stored or processed post-verification. The system meets ISO 27001 security standards and includes built-in privacy-by-design principles. For financial services, it supports PCI DSS requirements for strong authentication. Healthcare organizations benefit from minimal PHI exposure, while government deployments can meet FIPS 140-2 requirements through certified hardware security modules.
11. How does the zero-knowledge proof system work in practical terms?
Zero-knowledge proofs allow verification of identity without revealing any underlying biometric data. When you authenticate, the system cryptographically proves you possess the correct “key” (your face) without exposing facial features, images, or biometric templates to verifiers. Think of it like proving you know a password without revealing the password itself. This ensures verifiers can trust the authentication while knowing absolutely nothing about your physical characteristics.
12. What backup options exist if the primary face-based authentication fails?
SenseCrypt supports multi-modal authentication combining face recognition with optional passwords, PINs, or metadata. Organizations can configure fallback mechanisms such as manual verification processes, alternative biometrics (if available), or temporary access procedures. The system includes comprehensive audit logging to track authentication attempts and failures. For enterprise deployments, help desk procedures can assist with account recovery while maintaining security protocols.
13. How does SenseCrypt handle data sovereignty and cross-border data transfer requirements?
Since SenseCrypt stores no biometric data, most data localization requirements are automatically satisfied. SensePrints can be stored locally on user devices, in regional data centers, or distributed across blockchain networks as required by local regulations. The cryptographic nature of the credentials means they can cross borders without triggering biometric data transfer restrictions. Organizations can deploy on-premise solutions for complete data sovereignty control.
14. What training and support is provided during implementation?
Seventh Sense AI provides comprehensive developer documentation, integration guides, SDKs with sample code, and API references. Support options include knowledge base access, email/help desk support, phone support, and 24/7 live chat for enterprise customers. Training materials cover technical implementation, best practices, compliance considerations, and troubleshooting guides. Professional services are available for complex deployments, while standard implementations receive self-service resources and community support.
15. How does SenseCrypt perform compared to traditional password-based systems in terms of user experience?
SenseCrypt typically provides faster authentication (under 1 second vs. 15-30 seconds for password entry), eliminates password reset requests (reducing help desk costs by up to 70%), and achieves higher user satisfaction due to convenience. Users report preferring face-based authentication over passwords, OTP tokens, or traditional biometric systems that raise privacy concerns. The offline capability and cross-platform compatibility provide seamless experiences across web, mobile, and physical access points without the friction of remembering or managing multiple credentials.







One Comment